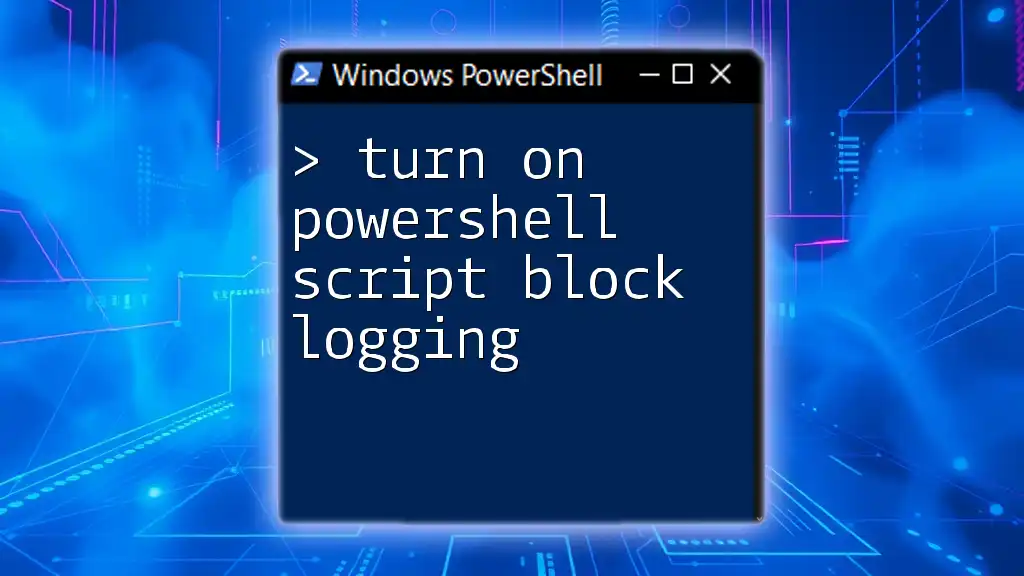
PowerShell script block logging captures the content of all executed script blocks, enabling detailed auditing and monitoring of PowerShell commands for enhanced security and compliance.
# Enable script block logging
Set-Item -Path 'HKLM:\Software\Policies\Microsoft\Windows\PowerShell\ScriptBlockLogging' -Value 1
What is PowerShell Script Block Logging?
PowerShell Script Block Logging is a feature that captures executed PowerShell commands and scripts, providing a detailed log of their execution. This functionality is critical for monitoring, auditing, and enhancing security within an organization. By logging script blocks, administrators can effectively track actions performed in PowerShell, offering insights into potentially unauthorized or harmful activities.
Why Use Script Block Logging?
In today's threat landscape, organizations must adopt robust security measures. PowerShell is a powerful tool but can also be misused for malicious purposes. By leveraging PowerShell Script Block Logging, businesses can enhance their security posture in several ways:
- Enhanced Visibility: Organizations gain visibility into script execution, allowing for better monitoring and response to suspicious activities.
- Auditing: The logs create a trail, which is valuable during audits and compliance checks, ensuring that all PowerShell usage is accounted for.
- Incident Response: When a security incident occurs, having detailed logs aids in forensic investigations and helps identify the root cause.
Understanding PowerShell and Its Security Model
Overview of PowerShell
PowerShell is a task automation framework from Microsoft, consisting of a command-line shell and an associated scripting language. Initially released in 2006, it has evolved significantly to become a robust tool for system administration and automation.
The Need for Enhanced Security
As PowerShell has grown in popularity, so has its use by attackers. Its ability to execute scripts and commands directly on an operating system makes it a prime target for exploitation. The implementation of logging is vital in creating an effective security model that monitors the usage of PowerShell and detects anomalies.
Enabling Script Block Logging
Configuring Script Block Logging in Group Policy
To enable PowerShell Script Block Logging, administrators can configure settings through the Group Policy Editor. Here’s how to access and set it up:
- Open the Group Policy Management Console.
- Navigate to Computer Configuration > Policies > Windows Settings > Security Settings > Advanced Audit Policy Configuration > Audit Policies.
- Locate Global Object Access Auditing, and then enable the script block logging setting by setting it to "Enabled".
Using PowerShell to Enable Script Block Logging
For those who prefer gaining control through PowerShell commands, you can enable script block logging directly with the following command:
Set-ItemProperty -Path "HKLM:\Software\Microsoft\PowerShell\1\PowerShellEngine" -Name EnableScriptBlockLogging -Value 1
This command modifies the registry to enable script block logging, providing a more technical approach for administrators comfortable with command-line interfaces.
What Happens When Script Block Logging is Enabled?
How PowerShell Logs Script Blocks
Once script block logging is enabled, PowerShell captures the contents of scripts and commands executed, even those that are run interactively. This means that anytime PowerShell interprets a command or script, a log entry is generated, detailing the command's content and execution context.
Log File Location
PowerShell logs these activities in the Event Viewer under:
Applications and Services Logs > Microsoft > Windows > PowerShell > Operational
You can access these logs using the Event Viewer to see detailed histories of script executions.
Analyzing the Logs
Reading the Script Block Logs
Analyzing the logs involves looking for patterns and specific entries that may indicate suspicious behavior. Each log entry typically includes:
- TimeCreated: When the script was executed.
- Id: Unique identifier for the event.
- Message: Contains details about the executed script block.
Utilizing PowerShell to Read Logs
To simplify log analysis, you can use PowerShell to retrieve and format the logs. Here’s a sample command:
Get-WinEvent -LogName 'Microsoft-Windows-PowerShell/Operational' | Select-Object TimeCreated, Id, Message
This command fetches relevant log entries, making it easier to visualize and filter the logs for specific events or keywords.
Case Studies and Real-World Examples
Example 1: Monitoring Suspicious Activity
In a recent case, an organization recorded unauthorized PowerShell activity that was flagged through script block logging. The logs revealed a series of encoded PowerShell commands, a common tactic used by attackers to obfuscate their actions. Thanks to the clarity provided by the logs, the security team quickly acted to neutralize the threat.
Example 2: Enhancing Compliance and Auditing
Another organization benefited from maintaining compliance with industry regulations by utilizing PowerShell script block logging for audit trails. The log details assisted the compliance team in demonstrating adherence to security policies during external audits, proving that proactive measures were in place.
Best Practices for Script Block Logging
Regular Monitoring and Reviews
To derive maximum value from script block logging, organizations should establish a routine for monitoring and reviewing the logs. Schedule regular audits to detect any anomalies or unauthorized script executions promptly.
Integrating with SIEM Solutions
Integrating PowerShell logs with Security Information and Event Management (SIEM) solutions enables organizations to correlate PowerShell activities with other security data. This integration improves overall security monitoring and response capabilities.
Training and Awareness
It is crucial to train staff about potential PowerShell threats and the importance of understanding script block logs. Enhance their awareness on how to identify malicious use cases and the processes to follow if suspicious activity is detected.
Common Pitfalls and Troubleshooting
Potential Issues with Script Block Logging
While enabling script block logging is beneficial, it does come with some challenges. These can include potential performance impacts due to the additional logging overhead and the risk of generating large log files that can become hard to manage.
Troubleshooting Tips
To overcome issues related to script block logging, consider the following tips:
- Ensure the logging feature is correctly configured, checking both Group Policy and registry settings.
- Regularly back up and archive log files to prevent storage issues.
- Monitor your systems for performance impacts after enabling logging, and adjust configurations if necessary.
Conclusion
PowerShell Script Block Logging is an essential feature for modern security practices, enabling organizations to monitor and trace PowerShell activity effectively. By implementing this feature, organizations can gain valuable insights into their PowerShell usage, enhance security monitoring, and comply with regulatory requirements.
Encouraging proactive measures and continuous training will further bolster an organization's defenses against potential threats. Now is the time to harness the power of PowerShell while keeping security front and center.
Additional Resources
For further exploration of PowerShell security practices, consider reviewing the official Microsoft documentation. This resource provides extensive information about security features, best practices, and tools available for effective PowerShell usage.