Certainly! Here's a concise explanation along with a code snippet in Markdown format:
To establish an SSH connection in PowerShell using a private key, you can utilize the `ssh` command followed by the username, target host, and specify the private key file.
ssh -i "C:\path\to\your\privatekey.pem" username@hostname
Understanding SSH and Private Keys
What is SSH?
SSH, or Secure Shell, is a protocol used to securely connect to remote systems over a potentially insecure network. It allows system administrators and users to remotely control machines, transfer files, and perform a multitude of tasks securely. The encryption that SSH provides makes it a fundamental tool for managing servers, especially in today's cybersecurity landscape.
The Role of Private Keys in SSH
SSH operates on a key-based authentication system that uses a pair of keys: a public key and a private key. The public key is placed on the server you want to connect to, while the private key remains with you. This method significantly enhances security, as it eliminates the need to send passwords over the network. Private keys are much harder to steal than passwords, making them a vital element of secure communications.
Setting Up PowerShell for SSH
Installing PowerShell
PowerShell is a versatile scripting language and command-line shell designed for system administration. It is included by default in Windows, but you can install it on other operating systems like macOS and Linux as well. For installation guides, refer to the official Microsoft documentation for your specific operating system.
Enabling OpenSSH in PowerShell
To use SSH in PowerShell, you need to ensure that the OpenSSH tool is enabled. On Windows, you can enable OpenSSH by running the following command in PowerShell:
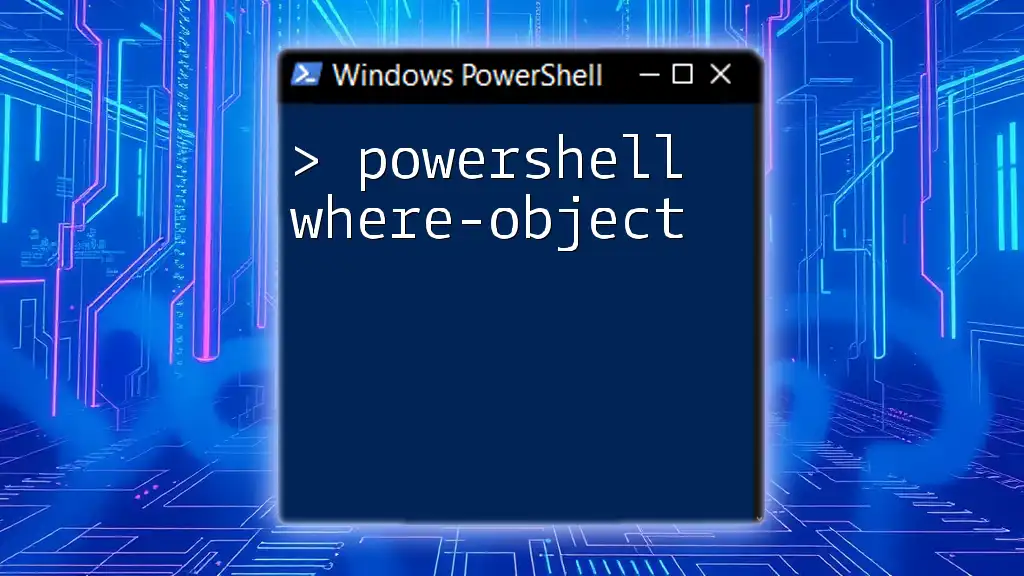
Get-WindowsCapability -Online | Where-Object Name -EQ "openssh.server*" | Add-WindowsCapability -Online
This command checks for OpenSSH components and installs them if they are missing. You can verify the installation by running:
Get-WindowsCapability -Online | Where-Object Name -EQ "openssh.server*"
A successful installation will show that the OpenSSH feature is installed.
Generating SSH Key Pair
Using PowerShell to Generate SSH Keys
Generating an SSH key pair in PowerShell is straightforward using the `ssh-keygen` command. Follow these steps:
- Open PowerShell.
- Run the following command to create a new SSH key pair:
ssh-keygen -t rsa -b 4096
In this command:
- `-t rsa` specifies the type of key to create, RSA (Rivest–Shamir–Adleman) is commonly used.
- `-b 4096` designates the number of bits in the key. A larger number means greater security.
When prompted, you can press Enter to accept the default file location or specify a different path. You will also have the option to enter a passphrase for an additional layer of security, which is highly recommended.
Saving and Securing Your Keys
Once generated, your SSH keys will be saved in the specified directory, typically under `~/.ssh/`. Ensure that you protect your private key by setting appropriate file permissions. On Windows, you can restrict access using PowerShell:
icacls path\to\your\privatekey /inheritance:r
icacls path\to\your\privatekey /grant YourUserName:(R)
Replace `path\to\your\privatekey` with the actual path and `YourUserName` with your account username. This limits access to your key file, keeping it secure.
Connecting to a Remote Server with SSH
Syntax of SSH Command in PowerShell
The syntax for connecting to a remote server using SSH in PowerShell is as follows:
ssh -i path/to/privatekey username@hostname
Here's what each part means:
- `-i path/to/privatekey` specifies the location of your private key.
- `username` is your account username on the remote server.
- `hostname` can be the IP address or the domain name of the server.
Step-by-Step Connection Process
To connect to a remote server, simply execute the command above in PowerShell. If you provided a passphrase during key generation, you will be prompted to enter it. Successful connections will grant you terminal access on the remote machine.
In the event of any connection issues, be prepared to troubleshoot common problems like incorrect paths or permissions associated with your private key.
Troubleshooting Common Issues
Permission Denied Errors
One of the most common issues users face is a "Permission denied" error when trying to connect. This can be due to several factors:
- The private key is not correctly located or has incorrect permissions.
- The username or hostname is incorrect.
- The public key has not been added to the server's `~/.ssh/authorized_keys` file.
To fix this, double-check the path to your private key and ensure that it has the right permissions.
Connection Timeout Problems
Timeout issues generally result from one of the following scenarios:
- The SSH service is not running on the server.
- Firewall settings are blocking the connection.
To troubleshoot, confirm that the SSH server is up and running, and check your local network configuration to ensure that there are no inbound or outbound rules preventing SSH communications.
Best Practices for Using SSH with Private Keys
Regularly Rotate Your Keys
For optimal security, rotate your SSH keys periodically. This minimizes the risk of key compromise and ensures that your access remains secure.
Use Passphrases for Added Security
Adding a passphrase to your private key provides an extra layer of protection. Even if someone gains access to your private key, they won't be able to use it without the passphrase.
Setting Up SSH Configurations
Using `~/.ssh/config` for Convenience
You can simplify your SSH connection process by creating a configuration file (`config`) in your `.ssh` directory. This allows you to set alias names for your server connections, reducing the complexity of the SSH command.
Here’s an example of what an entry in your `config` file could look like:
Host myserver
HostName example.com
User myusername
IdentityFile ~/.ssh/my_private_key
In this example:
- `Host myserver` allows you to connect using `ssh myserver` instead of the full command.
- `HostName` specifies the remote server.
- `User` indicates your username, and `IdentityFile` points to your specific private key.
Conclusion
Utilizing SSH with a private key in PowerShell provides a secure method of managing remote servers. By following the steps outlined in this guide, you can ensure a secure connection while adhering to best practices for key management. Whether you are a novice or an experienced administrator, these techniques will enhance your PowerShell experience and security posture.
Additional Resources
For those looking to further their knowledge, check out the official Microsoft PowerShell documentation and explore advanced tutorials related to SSH configurations and security practices. By continuously learning, you’ll become more proficient and confident in using PowerShell and SSH for your daily tasks.