To bypass the PowerShell execution policy temporarily for the current session, you can use the following command:
powershell -ExecutionPolicy Bypass -File YourScript.ps1
Understanding PowerShell Execution Policies
What Are Execution Policies?
Execution policies in PowerShell are safety features designed to control the execution of scripts and load configuration files. They help ensure that scripts are not executed without appropriate permissions, thereby protecting users and networks from potentially harmful scripts. The most common types of execution policies include:
- Restricted: The default setting that does not allow any scripts to run.
- AllSigned: Only scripts signed by a trusted publisher can be run.
- RemoteSigned: Requires any scripts downloaded from the internet to be signed by a trusted publisher before execution.
- Unrestricted: All scripts can run, but warnings are provided when running scripts downloaded from the internet.
Understanding these policies is crucial for anyone looking to use PowerShell effectively, especially for scripting and automation tasks.
Why Use Execution Policies?
The purpose of having execution policies in place is to enhance the security of the environment. By controlling which scripts can be run, you reduce the risk of executing malicious or unverified code. This is particularly important in enterprise environments, where the stakes are higher, and the potential damage from a harmful script can be significant.
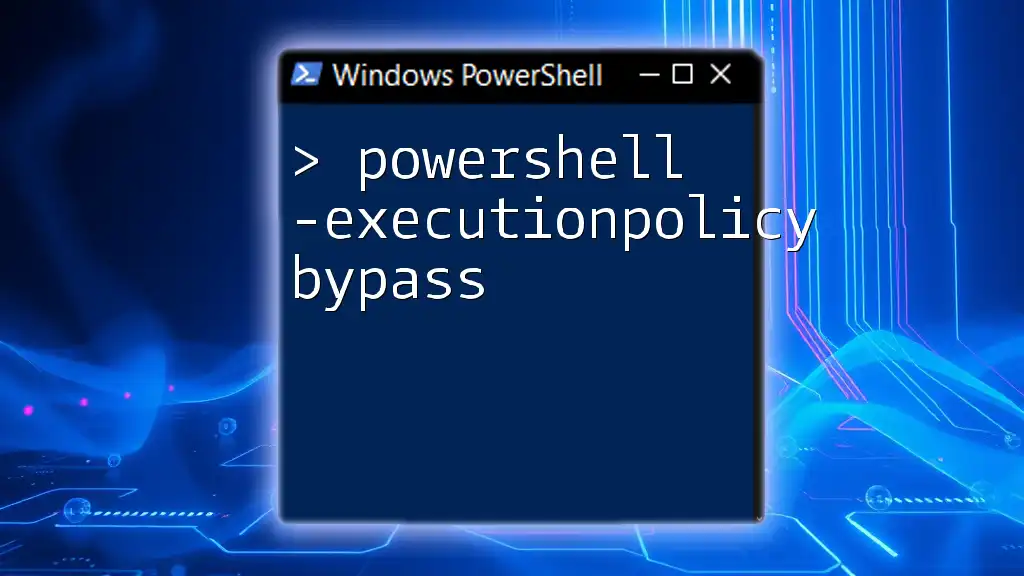
PowerShell Execution Policy Bypass
What Is Execution Policy Bypass?
Execution policy bypass refers to methods of circumventing the PowerShell execution policies that are set on a system. While these policies provide necessary security, there might be legitimate scenarios where a user needs to run a script that is not signed or is blocked by the current policy. Understanding how to bypass these policies can allow for more flexibility in scripting and automation processes.
The Risks Associated with Bypassing
Bypassing execution policies does come with its risks. When an execution policy is bypassed, there is a potential for malicious scripts to be run, leading to various security vulnerabilities. Therefore, it is essential to understand the implications of pushing through execution policies and to ensure that any scripts executed in this manner are from trusted sources. Always evaluate the security of the environment before deciding to bypass these safeguards.
Methods to Bypass PowerShell Execution Policy
Using the Command Line
One of the most straightforward methods to bypass execution policies is to modify the execution policy temporarily directly from the command line.
For instance, you can execute a script using the following command:
powershell -ExecutionPolicy Bypass -File "YourScript.ps1"
This command runs the `YourScript.ps1` file without regard for the current execution policy. It is effective for one-time script executions and allows you to avoid changing the policy settings permanently.
Using a Script Block
Another effective method involves using a PowerShell script block. This can be useful if you want to combine setting the policy and running scripts in a single command.
Here's an example of how this can be done:
& { Set-ExecutionPolicy Bypass -Scope Process; .\YourScript.ps1 }
In this snippet, the execution policy is changed to bypass only for the duration of the script's execution. By using the `-Scope Process` parameter, the policy applies only to the current PowerShell session and reverts back once the session is closed.
Utilizing PowerShell Profiles
You can also configure PowerShell profiles to load specific execution policies automatically. PowerShell profiles are script files that run whenever you start a new session. You can add a command to set a specific execution policy in your profile file. This approach is more persistent but should be used judiciously.
To modify your profile, you might add:
Set-ExecutionPolicy Bypass -Scope CurrentUser
This ensures that every time you launch PowerShell, the policy will be set to allow script execution for your user.
Setting the Execution Policy for Bypass
Permanent vs. Temporary Bypass
It's crucial to distinguish between a permanent and a temporary bypass of execution policies. A temporary bypass is what you achieve with the command line or script block methods outlined above, which apply only to the current session or script execution.
On the other hand, a permanent change can be made with the following command:
Set-ExecutionPolicy Bypass -Scope CurrentUser
This command sets the execution policy to bypass for the current user account permanently, allowing all scripts to run without restrictions. Ensure this is only done in trusted environments and with full awareness of the risks involved.
How to Revert the Changes
If you decide to revert to a more secure setting after bypassing, you can easily restore the default execution policy with commands like:
Set-ExecutionPolicy Restricted -Scope CurrentUser
This command will reinstate the default restrictive policy for your user account, enhancing your environment's security.
Best Practices for Bypassing Execution Policies
Understanding Your Environment
Before deciding to bypass execution policies, it’s essential to understand your environment thoroughly. Ask yourself questions such as: Is this a production environment? Are there compliance issues to consider? The answers will guide whether bypassing is a smart move.
Recommendations for Secure Scripting
When scripting in PowerShell, always adhere to secure coding practices. This includes sourcing scripts from trusted locations, validating input, and implementing error handling. Even when bypassing execution policies, a careful approach can minimize risks.
Logging and Monitoring
Maintaining logs and monitoring script execution can provide insight into activity within your environment. When running scripts with bypassed execution policies, consider logging actions to keep track of what is running and when. This is key to understanding and recovering from any unwanted changes made during script execution.
Conclusion
Bypassing PowerShell execution policies can provide flexibility and enable the complete potential of scripting in PowerShell, but it comes with inherent risks. Understanding how these policies work, utilizing safe methods to bypass them, and implementing best practices will contribute to a more secure scripting environment. Remember, the goal is to enjoy the benefits of PowerShell while maintaining a robust security posture.
Additional Resources
For more in-depth information about PowerShell execution policies and secure scripting practices, check out the official PowerShell documentation and related literature. Familiarizing yourself with best practices will enhance your ability to use PowerShell safely and effectively.
Call to Action
As you dive into the world of PowerShell, practice these concepts in a controlled environment, and consider joining our courses for comprehensive training on secure scripting techniques tailored for both new and experienced users of PowerShell.