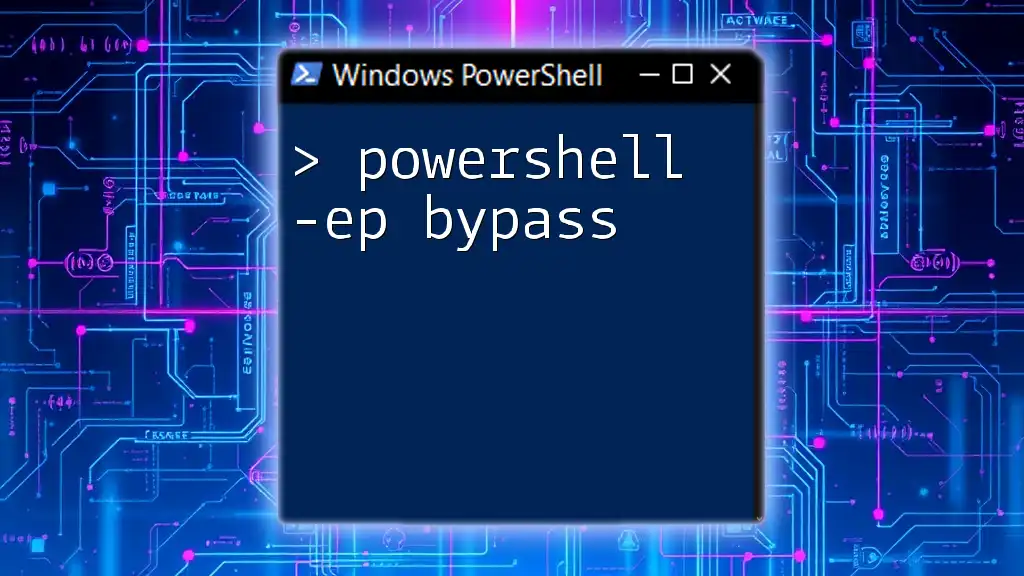
The command `powershell.exe -ExecutionPolicy Bypass` allows users to run PowerShell scripts without the restrictions imposed by the execution policy, which can be useful for executing scripts that may not be signed.
Here's the code snippet in markdown format:
powershell.exe -ExecutionPolicy Bypass -File "path\to\your\script.ps1"
Understanding Execution Policies
Definition of Execution Policies
Execution policies in PowerShell act as a safety mechanism to control the execution of scripts. They dictate whether scripts can run and under what conditions. Understanding these policies is crucial, especially for businesses and individuals who rely on automation. The five primary types of execution policies are:
- Restricted: Default setting that does not allow any scripts to run.
- AllSigned: Only scripts signed by a trusted publisher can be executed.
- RemoteSigned: All scripts downloaded from the internet must be signed by a trusted publisher.
- Unrestricted: All scripts can be run but warnings will prompt users before executing downloaded scripts.
- Bypass: No restrictions are imposed; all scripts can run.
Why Use `-ExecutionPolicy Bypass`?
The `-ExecutionPolicy Bypass` option is particularly useful in scenarios where you need to run scripts that might not meet a stricter policy setting. Common scenarios include:
- Running scripts downloaded from an unknown source that aren’t signed.
- Automating tasks on machines where adjusting the execution policy permanently is impractical.
- Running temporary scripts in environments where security policies are strict, but flexibility is needed occasionally.
Deep Dive into `powershell.exe -ExecutionPolicy Bypass`
The Command Structure
To effectively use `powershell.exe -executionpolicy bypass`, it’s essential to understand its command structure:
- `powershell.exe`: This calls the PowerShell application.
- `-ExecutionPolicy`: This parameter allows you to specify the execution policy in effect for the current session.
- `Bypass`: This indicates that no execution policy restrictions should apply.
Syntax Usage
Here's a basic syntax example to illustrate its usage:
powershell.exe -ExecutionPolicy Bypass -File "YourScript.ps1"
In this example:
- The `-File` parameter specifies the path to the script you wish to run.
- Using `Bypass` allows the script to execute regardless of any stricter execution policies that may be set on the machine.
Real-World Applications
Running Untrusted Scripts
At times, you may need to run scripts from external sources, which can often be untrusted. Using the `-ExecutionPolicy Bypass` allows for flexibility in this respect. For instance, if you receive a PowerShell script you need to execute but it is not signed, you can run:
powershell.exe -ExecutionPolicy Bypass -File "C:\Path\To\UntrustedScript.ps1"
Implications: Using this command can expose you to potential security threats. Always ensure you trust the source of the script before executing it.
Automating Tasks
The `-ExecutionPolicy Bypass` option shines in automation scenarios. For example, if your business generates daily reports, using scripts can save time. The command might look like:
powershell.exe -ExecutionPolicy Bypass -File "GenerateDailyReport.ps1"
This command executes a daily report generation script without hindrance from execution policy restrictions, ensuring that automation runs smoothly.
Security Considerations
Risks Associated with Bypass
While using `-ExecutionPolicy Bypass` grants immediate flexibility, it can open the door to security vulnerabilities. By running scripts without any restrictions, especially in a corporate environment, you may inadvertently execute malicious code. It's essential to remain vigilant about the origins of any scripts and to assess their content prior to execution.
Best Practices for Safe Execution
To minimize the risks, consider implementing the following best practices:
- Always verify source integrity: Ensure that any script you are running is from a trusted origin.
- Regularly sign scripts: If you frequently create your own scripts, consider signing them to avoid the necessity of using the Bypass option.
- Educate end-users: Conduct training sessions for employees on identifying potentially malicious scripts and adopting safe scripting practices.
Troubleshooting Common Issues
Common Errors with Execution Policies
Users often encounter errors when trying to execute scripts under restrictive execution policies. One common error is:
File C:\Path\To\YourScript.ps1 is not digitally signed.
This typically occurs when attempting to run a script without the appropriate execution rights.
How to Resolve These Issues
If you frequently run into the above error, using the `-ExecutionPolicy Bypass` allows for immediate resolution. However, if you prefer to adjust the policy temporarily, you can change the execution policy for a single PowerShell session with:
Set-ExecutionPolicy -Scope Process -ExecutionPolicy Bypass
This command sets the execution policy for the current session only, allowing scripts to run without modifying the system-wide policy settings.
Conclusion
Utilizing `powershell.exe -ExecutionPolicy Bypass` can greatly enhance your ability to run scripts in varied environments without restriction. However, it is crucial to balance the need for flexibility with the importance of security. Understanding the implications of execution policies, employing best practices, and staying informed about security risks will empower you to effectively navigate scripting challenges in PowerShell. Experimenting with these commands can enhance your proficiency and maximize the benefits of automation in your workflow.
Call to Action
As you continue your journey in PowerShell scripting, consider taking additional courses and participating in PowerShell communities to deepen your knowledge. Empower yourself to master the robust functionalities this powerful tool offers!
Additional Resources
For further exploration of execution policies, refer to the official Microsoft documentation on PowerShell execution policies, and join forums that discuss best practices and emerging trends. Engaging with others can provide deeper insights and enhance your skills in using PowerShell effectively.