In PowerShell, the "remote PowerShell port" usually refers to the default port 5985 for HTTP and 5986 for HTTPS used for PowerShell Remoting to connect to remote systems securely.
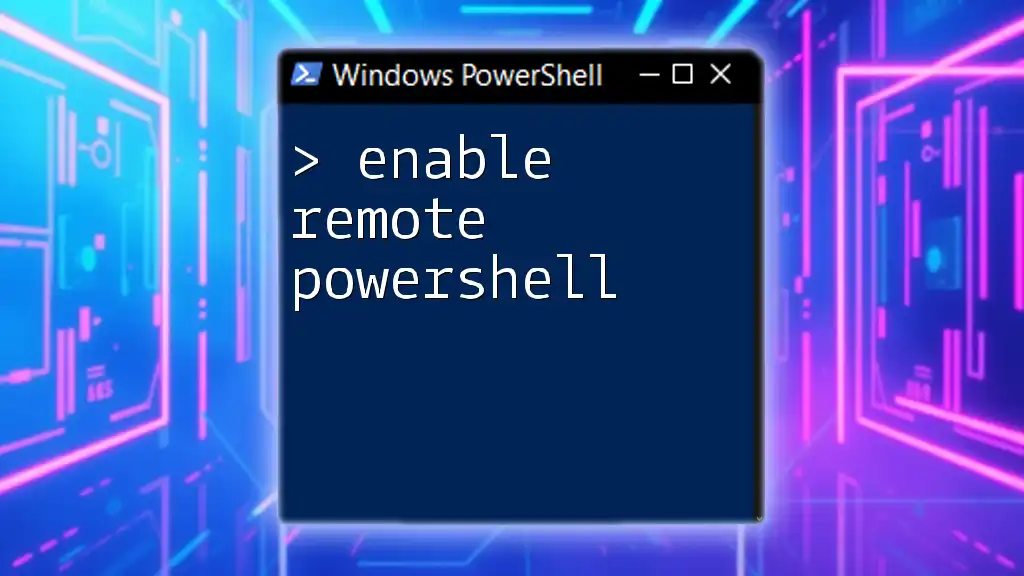
Here's a code snippet to enable PowerShell Remoting on the remote machine, ensuring the necessary ports are configured:
Enable-PSRemoting -Force
Overview of PowerShell Remoting
What is PowerShell Remoting?
PowerShell remoting allows you to execute commands and scripts on remote Windows machines, thus enabling centralized management across your network. This capability relies heavily on the Windows Remote Management (WinRM) protocol, making it possible to run commands remotely just as if you were logged in locally.
Benefits of Using PowerShell Remoting
The advantages of utilizing remote PowerShell include:
- Efficiency: Execute scripts on multiple systems simultaneously.
- Streamlined Management: Manage configurations, monitor systems, and automate tasks from a single location.
- Flexibility: Flexibly control various components and services across diverse environments.
Default PowerShell Remote Ports
Standard Ports Used for PowerShell Remoting
By default, PowerShell remoting operates over specific ports:
- HTTP (5985): The standard port for unencrypted connections.
- HTTPS (5986): The secure port for encrypted connections using SSL.
Incorporating secure protocols is crucial for protecting sensitive data transmitted over the network while executing administrative tasks.
Configurations for Different Environments
It is essential to recognize that the port configuration may vary based on the type of operating system:
- Windows Server: Often comes pre-configured to facilitate remoting for administrative tasks.
- Windows Desktop: May require additional setup to enable remote access.

Customizing PowerShell Remote Ports
Changing the Default Ports
Why Change the Default Ports? Changing the default ports can significantly enhance security, particularly in environments where exposing standard ports presents potential vulnerabilities.
How to Change PowerShell Remote Ports
To change remote PowerShell ports, you can utilize the following steps:
- Open PowerShell as an Administrator.
- Run the Command to Configure Port:
# Changing the default WSMan ports Set-WSManQuickConfig -Force Set-Item WSMan:\localhost\Service\Port 1234 # Example for HTTP
This command not only forces the configuration but also sets a new port for the WSMan service.

Testing Remote PowerShell Connections
How to Test Port Availability Before establishing a remote connection, you should confirm if the ports are accessible. Various tools and commands can assist in verifying port status:
-
Using Telnet: If you have Telnet installed, you can check connectivity by issuing the command:
telnet <RemoteComputer> 5985 -
Using PowerShell: A more integrated approach using PowerShell would involve:
Test-NetConnection -ComputerName <RemoteComputer> -Port 5985
This command provides a straightforward way to assess connectivity and will return details regarding the connection status.
Common Issues and Troubleshooting
The most common barriers to successful remote connections include:
- Firewall Configurations: Ensure that both the local and remote firewalls allow traffic through the designated ports.
- Network Profiles: Confirm that the network is classified as "Private" or "Domain" to permit remote connections.
If you receive errors such as "Access Denied," double-check administrative rights and user permissions on the remote machine.
Security Considerations with PowerShell Remote Ports
Understanding Security Risks
Understanding the associated security risks with remote connections is essential. Misconfigurations can expose your systems to threats such as unauthorized access and data breaches.
Best Practices for Securing PowerShell Remoting
To bolster security when utilizing remote PowerShell ports, adhere to the following best practices:
-
Utilize HTTPS over HTTP: Always opt for HTTPS to encrypt data in transit and protect sensitive information:
New-WebServiceProxy -Uri http://example.com -UseDefaultCredential -SSLSecurity -
Implement IP Restrictions: Restrict access to the remote PowerShell services by earlier defining an IP address list authorized for access.
-
Authenticate Users Properly: Use appropriate authentication methods, such as Kerberos or basic authentication, ensuring user credentials are secure during remote sessions.
Use Cases for PowerShell Remote Ports
Real-World Applications Remote PowerShell is widely utilized in various scenarios, such as:
- Automating System Updates: Administrators can easily push updates across the network without manual intervention.
- Monitoring Server Performance: Use scripts to gather performance metrics from remote servers, providing a comprehensive view of system health.
Case Studies Illustrating Improved Workflows
Consider a scenario in which a company struggled with inconsistent updates across its server fleet. By implementing a centralized PowerShell script executed via remote ports, the company automated its update process, reduced deployment time significantly, and improved system security through uniform governance.
Conclusion
In summary, mastering the remote PowerShell port is crucial for efficient system administration. Understanding how to configure, utilize, and secure remote connections can profoundly impact your workflow and system management capabilities. By applying the concepts outlined in this guide, you can enhance your PowerShell remoting practices and improve overall efficiency in managing your systems.
Additional Resources
For further exploration of PowerShell and WinRM, refer to the official Microsoft documentation and engage in community forums dedicated to PowerShell discussions to enhance your learning and troubleshooting experience.
FAQs
What should I do if I cannot connect over remote PowerShell? Check connectivity with commands mentioned earlier, review firewall settings, and ensure administrative permissions are in place.
How can I reset my PowerShell remoting configuration? Reset your configuration by executing the command:
Get-PSSessionConfiguration | Unregister-PSSessionConfiguration
Then re-enable remoting with:
Enable-PSRemoting -Force