A PowerShell downgrade attack involves exploiting vulnerable applications or services by forcing them to utilize older, less secure versions of protocols or commands, potentially allowing unauthorized access or actions.
# Example of initiating a downgrade attack by specifying an older version of a protocol
Invoke-WebRequest -Uri "http://example.com" -UseBasicP -Proxy "http://proxy:8080" -SkipCertificateCheck
What is a PowerShell Downgrade Attack?
A PowerShell downgrade attack refers to a technique where an attacker manipulates a system to revert to a previously less secure version of PowerShell or exploits outdated features of the scripting environment. This type of attack often capitalizes on the inherent backward compatibility of PowerShell versions, allowing malicious actors to introduce vulnerabilities that would not exist in the more secure, up-to-date versions.
In essence, by executing a downgrade attack, the attacker can gain unauthorized access to sensitive functions or commands by tricking the system into permitting outdated features that may lack current security patches or enhancements.
The Mechanics of a Downgrade Attack
How Downgrade Attacks Work
Downgrade attacks exploit trust or configuration flaws within the system. The attacker might employ man-in-the-middle (MITM) techniques, whereby they intercept and manipulate data being transmitted between PowerShell scripts or commands. For example, an attacker can force a system to accept an older, vulnerable version of a PowerShell module instead of a secure, updated version.
This manipulation can involve:
- Payload replacement: The attacker injects a malicious payload in place of an expected, legitimate payload.
- Version spoofing: The attacker uses tools to present themselves as a legitimate entity, deceiving PowerShell into accepting their commands.
Understanding how these attacks unfold is crucial for implementing effective countermeasures.
Environment Setup
A typical environment vulnerable to downgrade attacks may involve scenarios where outdated software or configurations exist. Attackers can gain footholds by exploiting systems that have not been regularly patched or where adaptive security measures are missing.
Necessary tools for executing and analyzing these attacks may include:
- Wireshark for network packet analysis.
- PowerShell scripts for manipulating versions or evaluating security settings.
Identifying Vulnerabilities
Understanding PowerShell Versions and Features
PowerShell has evolved significantly, introducing various security features across its versions. Each updated version offers enhancements and mitigation against prior vulnerabilities. However, the existence of backward compatibility means that developers and system administrators must be watchful for configurations that permit older, less secure versions to run.
Implications of enabling outdated scripts or modules can lead to severe consequences, such as unauthorized access or execution of malware. Understanding which versions are running on a system is vital to assess the risk of potential downgrade attacks.
Common Vulnerabilities Leading to Downgrade Attacks
Certain misconfigurations can create opening for attackers. For instance:
- Execution Policies: Using PowerShell's `-ExecutionPolicy` flag can inadvertently allow less secure command execution modes.
Example: If the execution policy is set to `Unrestricted`, it enables any script, including malicious ones, to run without restrictions:
Set-ExecutionPolicy Unrestricted -Scope CurrentUser
This setting poses a significant risk, as it bypasses useful security mechanisms intended to validate the integrity of scripts.
Preventing PowerShell Downgrade Attacks
Best Practices for PowerShell Security
To reduce the risk of downgrade attacks, it is imperative to adopt a security-first approach. Implementing the principle of least privilege ensures users have only the necessary permissions to complete their tasks. Additionally, regular patch management is essential to keep all software components, including PowerShell, up to date.
Security Configurations
Proper configuration of PowerShell settings significantly enhances security. It's crucial to set the execution policy to a more secure state:
Set-ExecutionPolicy AllSigned -Scope CurrentUser
This configuration only allows scripts signed by a trusted author to execute, effectively mitigating risks associated with unauthorized script execution.
Monitoring and Logging
Monitoring PowerShell activity and logging commands play an important role in identifying suspicious behavior. PowerShell provides built-in tools for logging:
- PowerShell Transcription can be used to capture all input and output for command sessions.
- Event Viewer helps in tracking execution logs that indicate the activity within PowerShell.
Establishing these monitoring practices enables administrators to detect anomalies and respond promptly to potential downgrading events.
Detecting Downgrade Attacks
Signs of a Downgrade Attack
Key indicators of a potential downgrade attack may include:
- Unexplained changes in command execution outcomes.
- Frequent alerts related to script execution failures.
- Unusual traffic or connections initiated from PowerShell environments.
Being vigilant and establishing clear signs of attack can significantly increase response efficiency.
PowerShell Scripts for Detection
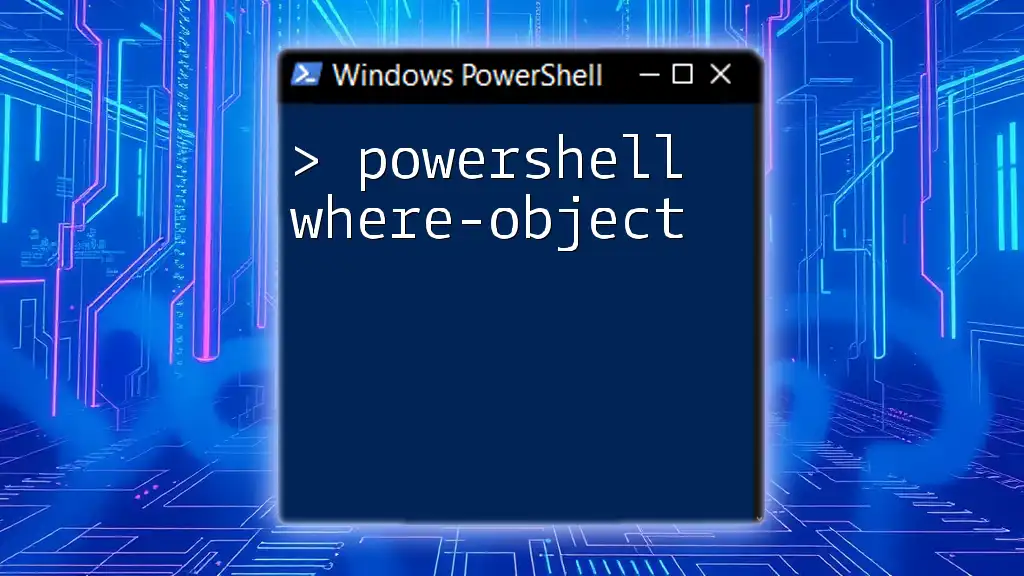
Detecting unusual PowerShell activity can be automated. Here’s a simple script to check for PowerShell events in the security log:
Get-EventLog -LogName Security | Where-Object { $_.Message -like "*PowerShell*" }
This command retrieves logs specifically associated with PowerShell, providing insight into suspicious activities and enhancing an organization’s response capabilities.
Case Studies
Real-World Examples of Downgrade Attacks
Several notable incidents highlight how PowerShell downgrade attacks can exploit system weaknesses. In one well-documented case, attackers utilized outdated modules to execute commands with elevated privileges, circumventing security features present in newer versions.
Lessons Learned
From analysis of these case studies, key takeaways emerge:
- Organizations must prioritize continuous software updates.
- Establishing robust monitoring mechanisms can thwart many attacks.
- Regular security assessments and audits help identify vulnerabilities before they are exploited.
Conclusion
In conclusion, PowerShell downgrade attacks illustrate a sophisticated threat landscape that demands proactive security measures. By understanding how these attacks function, recognizing vulnerabilities, and implementing best practices, organizations can significantly mitigate the risk associated with these threats. Continuous vigilance and updated security protocols remain essential in adapting to the ever-evolving nature of cybersecurity challenges.
References and Further Reading
For those looking to deepen their comprehension of PowerShell security and downgrade attacks, a variety of resources are available, including official documentation from Microsoft, security blogs, academic research, and community tools dedicated to PowerShell security assessments. Stay informed and empowered to protect your systems effectively.