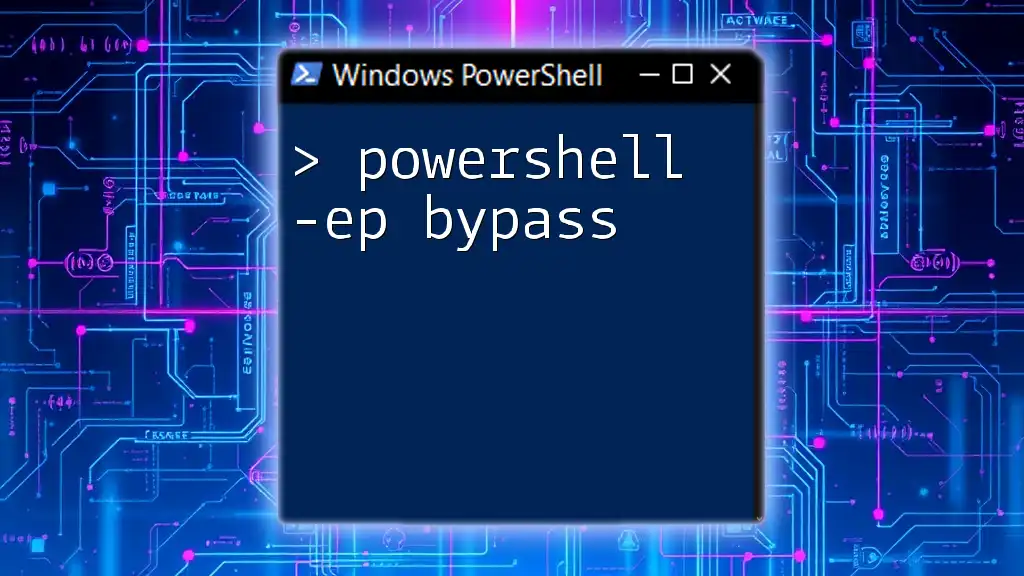
The command `powershell -ep bypass` allows you to launch a PowerShell session with an execution policy that permits the running of scripts without restriction, making it especially useful for executing scripts that might otherwise be blocked.
powershell -ep bypass
Understanding Execution Policies
What are Execution Policies?
Execution policies in PowerShell serve as a security feature designed to control the execution of scripts. They dictate which scripts are allowed to run within your PowerShell environment, thereby safeguarding your system from potentially harmful scripts. Understanding execution policies is crucial for both security and functionality.
Types of Execution Policies
There are various types of execution policies in PowerShell, each with different implications:
-
Restricted: This is the default setting, meaning no scripts can be run. It only allows interactive commands.
-
AllSigned: With this setting, all scripts must be digitally signed by a trusted publisher to execute. This allows the execution of scripts but ensures they are from a verified source.
-
RemoteSigned: This policy requires that scripts downloaded from the internet must have a valid signature. Locally created scripts can run without a signature, providing a balance between usability and security.
-
Unrestricted: There are no restrictions at all. Any script can run, which poses significant security risks but offers maximum flexibility.
-
Bypass: With this execution policy, PowerShell runs scripts without any restrictions or warnings. This is particularly useful in scenarios where the user wants to execute scripts quickly without needing to sign them.
The Need for -ExecutionPolicy Bypass
Common Scenarios Requiring Bypass
There are several instances where using the `-ExecutionPolicy Bypass` option is essential:
-
Automating Scripts: In environments where scripts must run unattended, such as automated deployment processes, the default restrictions often prevent necessary scripts from executing.
-
Testing Scripts: During development and testing phases, developers may not want to sign every script they create. The bypass option allows them to run their scripts without the need for a digital signature.
-
Running Downloaded Scripts: When downloading scripts from the internet, especially for quick use, it is impractical to go through the process of signing them every time. The bypass policy facilitates easier execution.
Risks and Considerations
While `-ExecutionPolicy Bypass` provides convenience, it also poses security vulnerabilities. Running unsigned scripts, especially those sourced from the internet, can lead to the execution of malicious code. Thus, it is essential to use this option judiciously. Always ensure that scripts are reviewed and trustworthy before execution.
How to Use PowerShell -ExecutionPolicy Bypass
Basic Syntax
The syntax for using the `-ExecutionPolicy Bypass` is straightforward. You would typically use it as follows:
powershell -ExecutionPolicy Bypass -File "C:\path\to\script.ps1"
Detailed Breakdown of the Command
PowerShell Command
The `powershell` keyword signifies that you are invoking the PowerShell command-line application.
ExecutionPolicy
The `-ExecutionPolicy` parameter specifies the execution policy you want to apply for that specific command invocation.
Bypass
Using the `Bypass` option indicates that you do not want any restrictions on the scripts that are being executed.
The Script Path
Make sure you specify the correct path to the script that you wish to execute. This is crucial, as PowerShell will not run the script if it can't find it.
Example Usage
Running a Sample Script
To illustrate, let's create a simple PowerShell script named `example.ps1`:
Write-Host "Hello, World!"
You would then execute this script with the bypass policy as follows:
powershell -ExecutionPolicy Bypass -File "C:\scripts\example.ps1"
Executing Inline Scripts
In some cases, you might want to run a one-liner script without creating a separate file. The `-Command` parameter can be leveraged here:
powershell -ExecutionPolicy Bypass -Command "Write-Host 'Hello from inline script!'"
Best Practices for Using -ExecutionPolicy Bypass
Script Validation and Testing
Before executing scripts with the `-ExecutionPolicy Bypass`, it is crucial to review and validate them. This means checking for any malicious code or unintended consequences. Particularly in production environments, one should always run scripts in a development environment first, ensuring they behave as expected.
Logging and Monitoring
Keeping track of script usage can help in auditing and maintaining security. Utilize logging mechanisms within your scripts to record when and how they were executed. This can be invaluable for identifying issues and ensuring accountability.
Alternate Methods to Bypass Execution Policies
Using Task Scheduler
An alternative to using `-ExecutionPolicy Bypass` in the command line is to create a scheduled task that can run your scripts with this policy. You can configure Task Scheduler to execute scripts according to your needs, which can ensure that they run without interruption while skipping the need for manual execution.
Creating a Shortcut
For frequent use, consider creating a desktop shortcut to simplify the execution process. You can create a shortcut that includes the full command, streamlining your workflow. The path in the shortcut would look something like this:
Target: C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe -ExecutionPolicy Bypass -File "C:\scripts\example.ps1"
Conclusion
In summary, understanding how to effectively use `powershdll powershell -ep bypass` can significantly enhance your ability to work with PowerShell scripts while navigating execution policies. However, it is imperative to remain aware of the security implications that come with bypassing execution policies. By adhering to best practices, validating scripts, and utilizing logging, you can strike a balance between convenience and security in your scripting endeavors.
Additional Resources
For further reading, consider exploring the official PowerShell documentation, which provides an exhaustive overview of execution policies and security practices. Additionally, look for reliable courses or tutorials that can expand your knowledge and skills in PowerShell.
Call to Action
We invite you to share your thoughts, experiences, or questions regarding the use of `-ExecutionPolicy Bypass`. Feel free to connect with us through our social media channels for more insightful PowerShell tips and tricks!