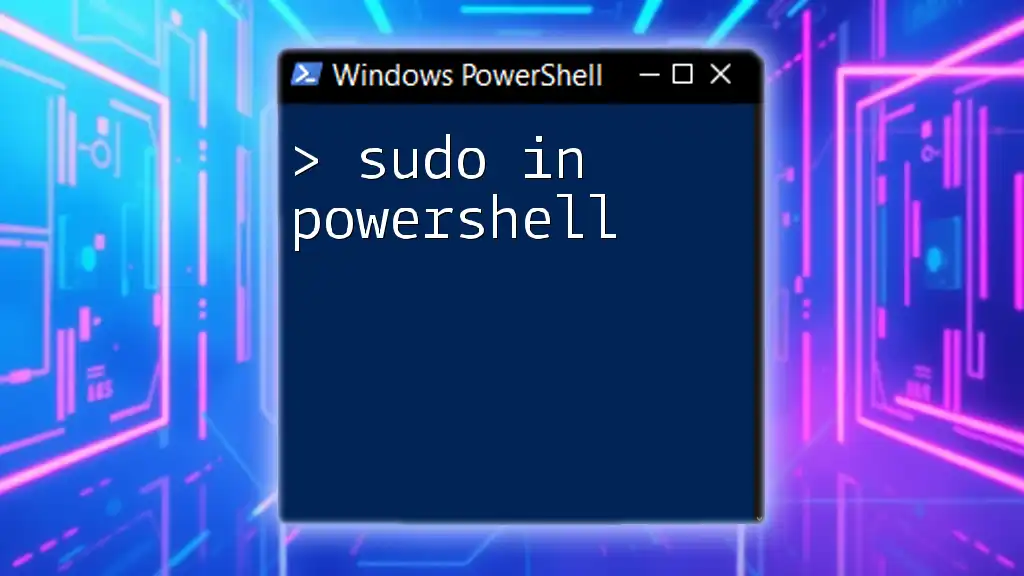
In PowerShell, the concept of "sudo" is achieved through the use of the `Start-Process` cmdlet with the `-Verb RunAs` parameter to execute commands with elevated privileges.
Start-Process powershell -Verb RunAs
The Role of Elevation in PowerShell
What Does Elevation Mean?
Elevation refers to the process of gaining higher privileges to execute commands that require administrative access. In command-line environments, not all operations can be performed by standard user accounts due to security constraints. Certain commands require elevated privileges to ensure system integrity and protect sensitive data.
How PowerShell Handles Elevated Privileges
User Account Control (UAC) plays a crucial role in managing permissions within Windows. When you attempt to run a command that requires elevated access, UAC prompts you to confirm your action. This safeguard helps prevent unauthorized changes to your computer. Users are prompted to consent, effectively acting as a layer of protection against potentially harmful commands.
Achieving Elevated Privileges in PowerShell
Running PowerShell as Administrator
To utilize elevated privileges in PowerShell, you first need to run PowerShell as an administrator. This process can be executed simply by:
- Using the Windows Start Menu: Search for “PowerShell” and right-click the icon to choose Run as administrator.
- Using the Context Menu: Alternatively, you can navigate to the PowerShell executable, right-click it, and select Run as administrator from the dropdown.
By opening PowerShell with administrator rights at the onset, you're empowered to execute commands that modify system settings or install software without additional prompts.
The 'Runas' Command
The Runas command is a built-in utility that allows you to run specific programs as a different user, including elevated permissions if necessary. The syntax is straightforward, but understanding its implementation is key. Below is an example of using `runas` to execute a PowerShell command as an administrator:
runas /user:Administrator "powershell.exe -Command Get-Process"
This command executes `Get-Process` with administrative privileges, showcasing how you can run commands on behalf of another user without logging in as that user.
Comparing PowerShell with 'Sudo'
Differences Between PowerShell and Linux's Sudo
The traditional 'sudo' command in Linux allows users to execute commands with elevated privileges, employing a straightforward format that grants temporary access without changing the user's account. PowerShell does not contain an exact equivalent to 'sudo', primarily due to its use of UAC and role-based access controls.
The Power of 'Start-Process' with Elevation
PowerShell’s `Start-Process` cmdlet allows you to start a new process with elevated permissions. This enables you to run applications or commands that typically require higher privileges seamlessly. Here’s an example of how to utilize `Start-Process` for elevated commands:
Start-Process PowerShell -Verb RunAs -ArgumentList '-NoProfile'
This command prompts a new instance of PowerShell to open in elevated mode, allowing you to execute additional commands without UAC intervention for each.
Practical Examples of Elevation in PowerShell
Common Scenarios where Elevation is Essential
There are numerous scenarios where elevated privileges are not just beneficial but essential:
- Installing Software: Many installations require administrative access for system integration.
For instance, to install a software package, you might use:
Start-Process msiexec.exe -ArgumentList '/i C:\Path\NameOfInstaller.msi /quiet'
- System Configuration Changes: Modifying settings in Windows often needs elevated commands. You can change execution policies using PowerShell:
Set-ExecutionPolicy RemoteSigned -Scope CurrentUser
This command allows scripts downloaded from the internet to run, provided they are signed by a trusted publisher.
Using Scripts that Require Elevation
Creating scripts that require elevation can streamline workflows. If your script requires elevated permissions, it's thoughtful to include code that prompts for elevation. The following script does just that:
if (-NOT ([Security.Principal.WindowsPrincipal] [Security.Principal.WindowsIdentity]::GetCurrent()).IsInRole([Security.Principal.WindowsBuiltInRole]::Administrator)) {
Start-Process PowerShell -ArgumentList "-File $PSCommandPath" -Verb RunAs
exit
}
This code checks if the script is running with administrative privileges. If not, it relaunches the script with the required permissions.
Security Implications of Running Commands as Administrator
Understanding Risks and Best Practices
While it can be essential to run commands as an administrator, doing so comes with its own risks. Executing unknown or untrusted commands with elevated access can lead to significant security vulnerabilities. It’s crucial to remain vigilant regarding which commands you run and from where they originate.
Best Practices for Using Elevation in PowerShell
- Limit the Use of Elevated Commands: Only use administrative privileges when absolutely necessary to minimize exposure to risk.
- Ensure Commands Are from Trusted Sources: Always verify the trustworthiness of scripts or commands before executing them, especially when running under elevated privileges.
Conclusion
In navigating the world of PowerShell, understanding how to achieve elevated privileges with commands analogous to ‘sudo’ in Linux is crucial. By mastering the techniques to run commands securely and effectively, you empower yourself to harness the full potential of PowerShell.

Call to Action
We encourage you to practice safely as you dive deeper into PowerShell. Join our courses to master PowerShell and subscribe for more insights on using commands effectively. Embrace the power of elevated permissions while adhering to best security practices!